Most businesses today face the threat of email spoofing, which can damage your brand’s reputation and compromise your communication. Implementing DomainKeys Identified Mail (DKIM) is an effective way to safeguard your emails and ensure that recipients can trust their authenticity. In this guide, you will learn the fundamentals of DKIM, how it operates, and the necessary steps to set it up, enabling you to enhance your email security and protect your brand from potential fraud.
Key Takeaways:
- DKIM (DomainKeys Identified Mail) is an email authentication method that helps verify the sender’s identity and ensures message integrity.
- Implementing DKIM involves adding a digital signature to outgoing emails, which can be validated by the recipient’s mail server against the sender’s public key stored in DNS.
- By using DKIM, brands can significantly reduce the risk of email spoofing, protecting their reputation and maintaining customer trust.
- DKIM works in conjunction with SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance) for enhanced email security.
- Regular monitoring and maintaining DKIM records is necessary to ensure continued effectiveness and adapt to any changes in email practices.
Decoding DKIM: The Vital Role of Email Authentication
What is DKIM and Why Does It Matter?
DKIM, or DomainKeys Identified Mail, is an advanced email authentication technique that adds a verified digital signature to your emails. By implementing DKIM, you help ensure that the messages sent from your domain are legitimate, making it harder for cybercriminals to spoof your brand. This method not only enhances your email deliverability but also plays a pivotal role in building trust with your recipients. A successful DKIM implementation can significantly reduce the chances of your emails being marked as spam or falling victim to phishing attacks.
The Mechanics of DKIM: How It Works Behind the Scenes
DKIM operates by attaching a unique signature to your outgoing email headers. This signature is created using an encryption algorithm that corresponds to a public key published in your domain’s DNS records. When the recipient’s mail server receives the email, it retrieves this public key, verifying the signature against the email’s content. If they match, the email is confirmed as authentic and from you, increasing the likelihood that it will land in the recipient’s inbox without being flagged.
The DKIM process begins when you send an email from your domain. Your email server utilizes a private key to generate a hash of the message, which gets appended as a DKIM-Signature header. This ensures any alterations to the email will lead to a signature mismatch. The public key necessary for verification is stored in your DNS records, accessible to recipient servers. Upon receiving your email, the recipient’s server checks your domain’s DNS records to find the public key, using it to verify the DKIM signature. Only if the signature is valid does the server accept the email as legitimate. This sophisticated chain of events not only protects your brand from spoofing but also fosters a sense of security and reliability among your customers.
The Stakes: Brand Reputation and Email Spoofing Risks
Email spoofing poses significant threats to your brand’s reputation, compromising customer trust and potentially leading to financial loss. Spoofed emails can deceive recipients into sharing sensitive information or completing unwanted transactions, creating a ripple effect of distrust that impacts your entire customer base. The consequences stretch beyond immediate losses—the erosion of reputation can take years to rebuild, leaving your organization vulnerable to ongoing phishing attempts and diminishing brand loyalty.
The Consequences of Failing to Implement DKIM
Neglecting DKIM implementation exposes your brand to a wide array of risks, including unauthorized access to sensitive data, decreased deliverability of your legitimate emails, and irreversible harm to your reputation. As unsuspecting customers fall prey to spoofed emails, they may not only lose trust in your communications but also take their business elsewhere. Long-term brand perception can suffer as consumers gravitate towards competitors they believe offer more secure interactions.
Real-World Examples of Brand Damage Due to Spoofing
Numerous companies have faced significant backlash due to incidents of email spoofing, resulting in financial and reputational damage. Major organizations like Microsoft and PayPal have experienced instances where cybercriminals impersonated their brands, leading to millions in losses and compromised user data. These real-world scenarios emphasize the critical need for robust email authentication measures like DKIM to protect both your brand and your customers.
In one prominent case, a spoofed email masquerading as a PayPal notification tricked thousands of users into providing their login credentials, leading to significant financial theft and a devastating loss of customer trust. Similarly, Microsoft dealt with widespread phishing attacks that leveraged their trusted name, resulting in an uptick in credential theft and a complicated recovery process. These incidents starkly illustrate that failing to implement DKIM not only exposes your brand to damaging exploits but also creates a long-lasting impact on consumer perception and loyalty.
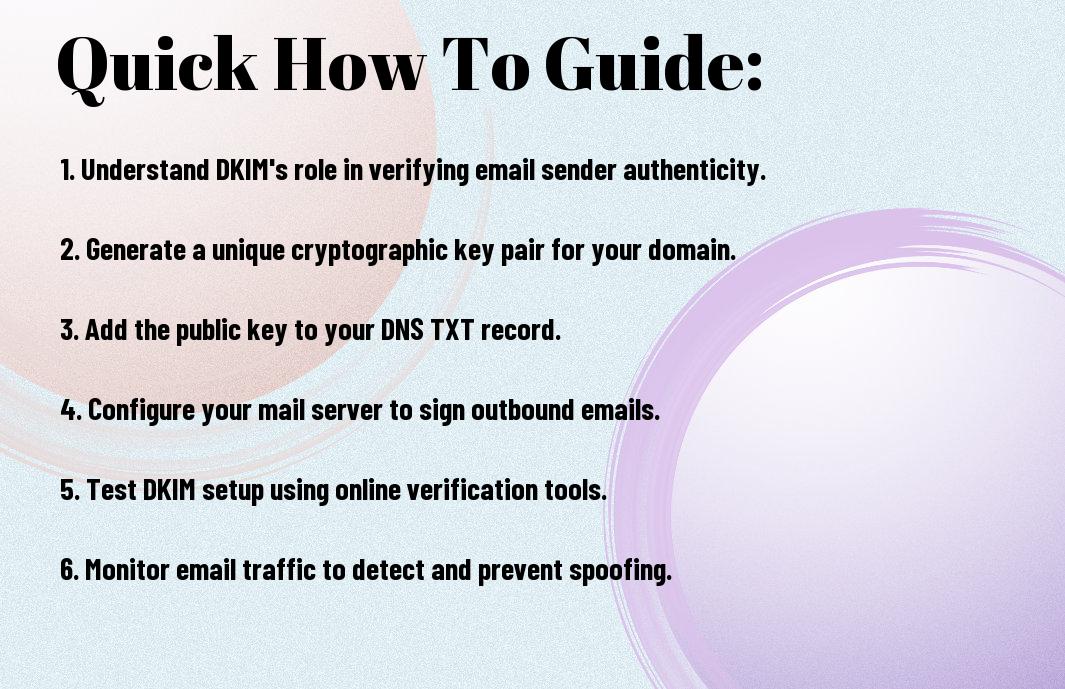
Implementing DKIM: A Step-by-Step Guide
| Step | Description |
| 1. Preparing Your Domain for DKIM Setup | Ensure your domain is properly configured and that you have access to your DNS settings. |
| 2. Configuring DKIM with Your Email Provider | Generate DKIM keys through your email provider and update DNS records. |
Preparing Your Domain for DKIM Setup
Start by verifying that your domain is active and fully set up. You should have control over your DNS records since DKIM requires the addition of specific TXT records. Ensure your email system is configured to send messages from this domain to avoid complications during the setup process.
Configuring DKIM with Your Email Provider
Access the DKIM configuration settings offered by your email service provider. They typically provide an option to generate your public and private key pair. The private key will reside on your sending server while the public key must be added to your domain’s DNS records. This allows receiving servers to verify the legitimacy of your emails.
Once you generate the keys, you’ll find instructions specific to your provider, which may require you to copy the public key and create a TXT record in your DNS settings. This entry should include your selector, domain, and the public key string. Be sure to allow adequate time for DNS propagation after making changes, which can usually take up to 48 hours. Testing tools are available to check the DKIM setup post-implementation, helping you confirm that your emails are being properly authenticated before they hit recipients’ inboxes.

Beyond DKIM: Holistic Strategies for Email Security
Implementing DKIM is just one piece of the puzzle; a comprehensive approach to email security involves multiple layers. By integrating other authentication protocols and best practices, you can fortify your defenses against various threats. Combining DKIM with SPF and DMARC provides a robust shield that not only verifies the sender’s identity but also helps you enforce policies regarding how receiving mail servers handle potentially fraudulent emails.
The Interplay of DKIM with SPF and DMARC
DKIM works in tandem with SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting & Conformance) to create a secure email environment. While DKIM verifies the authenticity of the email sender through cryptographic signatures, SPF allows domain owners to specify which servers are authorized to send emails. DMARC builds upon both, providing the policy framework for handling messages that fail DKIM or SPF checks, enabling you to reject or quarantine suspicious emails effectively.
Best Practices for Maintaining Email Integrity
To maintain the integrity of your email communications, incorporate several best practices into your email security strategy. Regularly audit your SPF records to ensure they accurately reflect your current sending sources and review your DKIM settings to keep them up to date. Implement DMARC reporting to gain insights on how your emails are treated by recipient servers, allowing you to identify and respond to potential issues proactively.
Enhancing email integrity doesn’t stop with basic configurations. Conducting periodic security training for your staff helps them recognize phishing attempts and suspicious messages. Enforce the use of strong passwords and two-factor authentication (2FA) for accounts associated with your email domain. Additionally, using a dedicated IP address for your email campaigns can further improve your sender reputation and thereby your email deliverability. By continually adapting to the evolving landscape of email threats, you ensure your brand remains protected against deceptive practices.

Monitoring and Adapting Your DKIM Strategy
Establishing DKIM is just the starting point; continuous monitoring and adaptation are vital to ensure its effectiveness. You need to keep an eye on email deliverability rates and assess how well your DKIM signatures are performing. By regularly reviewing these metrics, you can identify any weaknesses in your current setup and make timely adjustments to enhance your email security posture.
Tools for Tracking DKIM Performance and Issues
Utilizing specific tools enables you to effectively track your DKIM performance and identify any issues. Tools like MXToolbox and DKIMValidator allow you to diagnose DKIM signatures, check if they are set up correctly, and analyze the signing process. These platforms provide valuable insights, including any failed verifications, which can help you pinpoint errors and ensure successful email authentication.
Regular Updates: Keeping Your DKIM Setup Robust
Regular updates are key to maintaining a robust DKIM setup. Email technology and threat vectors evolve continuously, making it vital to stay informed about updates and best practices. Periodically changing your DKIM keys, as well as revisiting your DNS records to ensure they are current, fortifies your defenses. Staying engaged with industry developments equips you to address any emerging vulnerabilities promptly and effectively.
Having an established routine for updating your DKIM setup not only involves adjusting the keys but also periodic audits of your DNS entries and configurations. Ensure you are using secure algorithms, such as SHA-256, and review your DKIM expiration policies. Maintaining documentation regarding your DKIM settings and their revisions can help track changes over time and simplify problem-solving when issues arise. These measures cultivate a proactive approach toward email security, augmenting your brand’s credibility and reliability.
To wrap up
Following this guide on DKIM, you should now understand how implementing this authentication method can significantly protect your brand from email spoofing. By ensuring integrity and authenticity in your email communications, you can build trust with your recipients and safeguard your reputation. Taking proactive steps to enhance your email security not only benefits your organization but also contributes to a more reliable email ecosystem for everyone. Start integrating DKIM today to fortify your defenses against malicious actors.
FAQ
Q: What is DKIM and how does it work?
A: DKIM, or DomainKeys Identified Mail, is an email authentication method that allows the sender to sign their emails with a unique digital signature. This signature verifies that the email was indeed sent by the domain it claims to be sent from and that it hasn’t been altered during transmission. When a recipient’s email server receives a DKIM-signed email, it checks the signature against the public key published in the sender’s DNS records. If the signature matches, the email is considered authentic; if not, it may be flagged as suspicious.
Q: Why is DKIM important for protecting my brand?
A: Implementing DKIM helps safeguard your brand’s reputation by preventing email spoofing, where malicious actors impersonate your domain to send fraudulent messages. This form of identity theft can damage your brand’s credibility and impact customer trust. By using DKIM, you establish a layer of protection that enhances your email deliverability and helps ensure that customers receive legitimate communications from your organization.
Q: How do I set up DKIM for my domain?
A: To set up DKIM, you need to generate a key pair (a public and private key). The private key is used by your email server to sign outgoing messages, while the public key is added to your domain’s DNS records. The typical steps include: 1) generating the DKIM key pair using your email service provider’s tools; 2) adding a TXT record containing the public key to your DNS; 3) configuring your email server to sign outgoing emails with the private key. It’s also advisable to test the setup to ensure it is working correctly.
Q: Can DKIM completely eliminate email spoofing?
A: While DKIM significantly reduces the risk of email spoofing, it is not a standalone solution. It is most effective when combined with other authentication methods such as SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting & Conformance). These methods work together to improve email security. Therefore, implementing a multi-layered approach bolsters protection against spoofing attacks, phishing attempts, and other email-based threats.
Q: How can I check if DKIM is working for my email domain?
A: You can verify your DKIM setup by sending an email to a third-party service or using tools designed for this purpose. When you send a test email, these services will analyze the email headers to confirm if the DKIM signature is present and valid. Additionally, you can inspect the email headers manually in your email client. Look for the ‘DKIM-Signature’ field, and ensure that the status indicates “pass.” Some popular online tools, such as MXToolbox or DKIMValidator, can also assist in checking your DKIM settings effectively.

